What
are users in the operating system?
A user is a person who accesses or
utilizes computer resources or network services. In order to gain access to a
computer system, user are required to log-in to an operating system. Each and
every file or folder is owned by a particular user.
There are three types of users in the
Linux operating system root or superuser, regular user, and system user.
· Root user
(superuser): When the Linux is installed on computer the root account
is created by default you just need to set a password to enable the root
account which is also known as superuser. The root user is the most privileged
user who can access all commands, files, and all services.
· Regular user: A regular user
has only the necessary privileges to perform standard tasks such as creating
folders, etc. They can store files in their own home directory and have to work
only in their home directory. Since the regular user does not have root user
privileges they cannot delete or modify system configuration files or other
critical files.
· System user: System users are
the software or application user created automatically by the system to run
services such as mail, apache, ftp, etc have their own individual system
account. It is also known as a service user. These accounts exist to allow each
of these services to interact with the computer
Important files
· /etc/passwd: This file contains information about users. It is a text-based file. The passwd file is stored under “etc” directory.
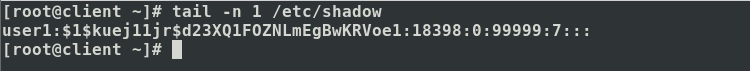
· /etc/shadow: This file contain
the actual password in an encrypted format. This shadow file is also stored
under “etc” directory.
The above two files can be view by regular
file viewer, cat, less, more or tail command, etc.
Ø To know more about
the above two files click here.
Managing
local user
1. useradd command: This command is used to create a new user account. This command does not set any valid password and the user cannot log-in to the account until the password is set.
From the above example, you can see the user Ronak is successfully created but we did not get any notification that the user Ronak is created. So if you want to check whether the user Ronak is created or not just check “/etc/passwd” file and the example is given below.
2. Passwd command: The newly created user account has no password. This command is used to add a password to the new user account and this same command is used to change the password of an existing user account.
The password is successfully given to
Ronak. But you can see “New password and Retype new password” is seems empty
this feature is by default in the Linux operating system. You just have to type
your password as per your requirement it will not appear but it will take your
new password.
3. usermod command: To modify an existing user account usermod command is used.
From the above example you can see –u
option is used for changing UID. By
using the “usermod” command the UID is successfully changed from 1003 to 1005
for Ronak.
4. userdel command: The userdel command is used to delete an existing user account and it related files
From the above example, you can see userdel
command is used with option –r stands for recursively and –f is for
forcefully and this both options can be used together like –rf.
Note: Regular user or
normal user cannot execute the above commands and if you try to execute with
the regular user it will give you permission denied error. All the above
commands can execute by the root user or sudo user only.
What
is the groups?
The main purpose of the group is to set a
privilege like read, write, or execute permission to the files or resources
that can be shared among the users within the group. In a single group, there
can be multiple users. Basically groups are a collection of users. In Linux
every user has a UID (user identifier) and a GID (Group identifier).
There
are two types of groups:
Primary
groups
Normally, when a new user is created a new
group is also created automatically while creating a new user. A new group has
the name and GID (group ID) same as the user name and UID (user ID). A new user
becomes a member of its own group which becomes a primary group for the user.
The newly created user is the only member of this (UPG) user private group.
·
Every user has one primary group.
·
For the local user, the primary group is defined by the GID
number of the group listed in the fourth field of “/etc/passwd”.
Supplementary
groups
A supplementary group is an additional
group the user can become a member. For example, a newly created user john
automatically becomes a part of the group name john but if john wants to access
files owned by the group name rocky in that case john has to be a member of the
group rocky to access those files. So john becomes a member of the group name
rocky which is a supplementary group.
·
The User may be a member of zero or more supplementary
groups.
·
The user’s that are members of the supplementary groups are
listed in the last field of the group’s entry in “/etc/group”. The user who is members of the groups is
determined by a comma-separated list of users found in the group’s entry in
“/etc/group” file.
Important
file
· /etc/group: This file is a
text file that contains the group information for each user account.
The above file can be view by regular
file viewer, cat, less, more or tail command, etc.
Ø To know more about
the above file click here.
Managing
local group
1. groupadd command: This command is used to create groups and by writing it without option the next available GID (group identifier) from the range specified in the “/etc/login.defs” file.
By using “groupadd” command new group is
created with the name hockey and the new group hockey is created with GID 1003.
The fourth field is empty because no user is added to hockey group.
2. groupmod command: This command is used to change an existing group name and GID. The –n option is used to specify a new name to an existing group. The option –g is used to specify your own GID number to the existing group.
By using “groupmod” command you can see
that the GID of the group hockey is been changed from 1003 to 8000.
3. groupdel command: The groupdel command is used to remove the existing group.
From the above example by using “groupdel”
command the group hockey is successfully deleted.
Note: usermod alters
group membership. You can change the user’s primary group with “usermod –g
groupname” command. To add an existing user to a supplementary group “usermod
–aG groupname username” command is used.
UID
and GID:
UID: A UID (user
identifier) is a unique number that Linux operating system assigned to each
user. Which is used to identify the user on the system and to determine which
system resources the user can access.
There are some specific ranges of UID are
used for a specific purpose are given below.
·
The UID 0 is only assigned to the superuser account, root.
·
The UID 1 – 200 is a range of “system users” assigned
statically to system processes.
·
The UID range 201 – 999 is a range of “system users” used
by system processes that do not own files on the system.
·
The range of UID 1000+ is available to assign to the
regular users and the maximum range is 60,000 for assign to regular users.
GID: A GID (group
identifier) is a unique number to identify each group.
There are some specific ranges of GID are
used for a specific purpose are given below.
·
The GID 0 is only assigned to the superuser account, root.
·
The GID 1 – 200 is a range of “system users” assigned
statically to system processes just like UID.
·
The GID range 201 – 999 is a range same as UID used for
“system user” used by system processes that do not own files on the system.
·
The range of GID 1000+ is available to assign to the
regular users and the maximum range is 60,000 for assign to regular users.
Note: Default ranges
used by useradd and groupadd can be changed in the “/etc/login.defs” file.