/etc/passwd:
This file contains information about users. It is a text-based file with seven fields separated by a colon (:). This file in stored under “etc” directory and to view this file we can use regular file viewer, cat, less, more or tail command, etc.
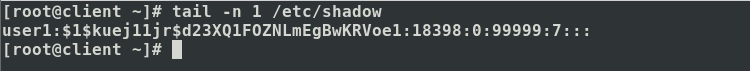
From the above image, the tail command is used along with –n option followed by 1 which means only one line from the bottom of this file.
Basically tail command is used to view a specific number of lines as per need. Here –n option stands for a number.
Note: The “/etc/passwd” file can be
accessed by a normal user there is no need to gain root access.
username:password:UID:GID:GECOS:/home/user:default shell
Breaking down of the user entry from left
to right:
1. Username is a mapping of a
UID which uniquely identifies the user on the computer system.
2. Password is where
passwords were kept in an encrypted format but display only “X”. The full
encrypted password is stored in a separate file called “/etc/shadow”.
3. UID is a user ID, a
number that identifies the user at the most fundamental level.
4. GID is a user’s
primary group ID number.
5. GECOS field usually
includes the user’s full name, or address, or phone number, or any basic
information, and this field is also known as the comment field.
6. /home/user is the location
of a user home directory, personal data, and configuration files.
7. Shell is a program that
runs as the user logs in. For a regular user, this is normally the program that
provides the user’s command interpreter.
/etc/shadow:
This file stores the actual password in encrypted format using a hashing algorithm and also holds information about password aging. It is a text-based file with nine fields separated by a colon (:).
Note: Root access is required to view “/etc/shadow” file. If you try to view this file as a normal user the shell will throw an error message given below.
Output after taking root access.
Breaking down the entry from left to
right:
1. Login name: The login name of
the user which is store on the system.
2. Encrypted password:
A
password field starts with an exclamation ($) mark which means that the
password is locked.
3. Last password change: This field shows
the date of the last password changes, represented as the number of days since
1970/01/01.
4. Minimum: The minimum
number of days before a password may be changed, where 0 means “no minimum age
requirement”.
5. Maximum: This field shows
the maximum number of days before a password must be changed.
6. Warning period: The warning
period that a password is about to expire. Represented in days, where 0 means
“no warning given”.
7. Inactive period: The number of days
a user account remains active after a password has expired. A user may still
log into the system and change the password during this period. After the
specified number of days, the account is locked and becoming inactive.
8. Expiration date: This field shows
the expiration date of the user account represented as the number of days
since 1970/01/01.
9. Blank: This field is
blank. It is reserved for future use.






No comments:
Post a Comment